COMP2310/COMP6310:
Concurrent and Distributed Systems
Semester 2 2014
Final Exam
Writing period: 3 hours duration
Study Period: 15 minutes duration
Permitted Materials: One A4 page with handwritten notes on both sides.
Questions are NOT equally weighted. Marks total 100.
This exam will contribute 50% to your final assessment.
For the exam, your home directory will contain sub-directories
Q1, Q2, ..., Q6. You must put your answers to
Questions 1 to 6 in the indicated files in these sub-directories.
The marking scheme will put a high value on clarity so, as a general
guide, it is better to give fewer answers in a clear manner than to
outline a greater number in a sketchy, half-answered fashion.
Please use a spell-checker (e.g. ispell or aspell)
on your answer files to ensure your answers are clear.
There will be some questions whose answer (for full marks) will
require a syntactically and semantically correct program (e.g. in
FSP, Java, C). For such questions pseudo-code may still earn some
marks.
If you have technical difficulties (apart from answering the questions
themselves), request assistance.
while (1) { // thread 0
// non-critical section 0
...
while (inCS1==1) {/*spin*/}
inCS0 = 1;
// critical section 0
...
inCS0 = 0;
}
| | | | | | | |
| | | | | | | |
|
while (1) { // thread 1
// non-critical section 1
...
while (inCS0==1) {/*spin*/}
inCS1 = 1;
// critical section 1
...
inCS1 = 0;
}
|
- Model the algorithm in FSP, capturing the essential characteristics
for mutual exclusion.
Place your answer in the file Q3/mutex.lts.
[5 marks]
Hint: an FSP process will model each thread. For each thread,
model the execution of critical regions by the sequence
crit.enter and crit.exit; that of the non-critical section as
simply noncrit. The variables can be
modelled as inCS0:VAR and inCS1:VAR, where
set VarAlpha = {read[0..1], write[0..1]}
VAR = VAR[0],
VAR[i:0..1] = ( read[i] -> VAR[i]
| write[j:0..1] -> VAR[j] ).
Note also that the alphabets of the processes for each thread should
be extended by inCS0, inCS1}.VarAlpha before being
composed into the final system.
- Does the algorithm ensure mutual exclusion? If so, briefly
explain why. If not, state a sequence of actions (preferably in the
form of a trace, the shorter the better) which shows how it is
violated.
Place your answer in the file Q3/Q3.txt.
[2 marks]
- Specify an FSP safety property and a composition using this property
which could be used to formally
check whether mutual exclusion is in fact preserved.
Place your answer in the file Q3/mutex.lts.
[2 marks]
- Can the algorithm deadlock? Briefly explain why or why not.
Place your answer in the file Q3/Q3.txt.
[3 marks]
- COMP6310 students, answer the following:
Specify FSP progress property(ies) which states that, once a
thread is waiting to enter its critical region, it will eventually
be allowed to enter.
Place your answer in the file Q3/mutex.lts.
Briefly explain whether you expect it to be violated,
i.e. whether starvation is possible.
Place your answer in the file Q3/Q3.txt.
COMP2310 students only: Briefly explain whether you expect the
algorithm has the property that, once a thread is waiting to enter
its critical region, it will (always) eventually be allowed to enter.
Place your answer in the file Q3/Q3.txt.
[3 marks]
QUESTION 4: Message Passing [14 marks]
A bounded buffer can be specified in FSP as
BUFFER(N=5) = COUNT[0],
COUNT[ct:0..N] = ( when (ct < N) put -> COUNT[ct+1]
| when (ct > 0) get -> COUNT[ct-1]).
PRODUCER = ( put -> PRODUCER ).
CONSUMER = ( get -> CONSUMER ).
||BOUNDEDBUFFER = (PRODUCER || BUFFER(5) || CONSUMER).
Write a working implementation of this system using synchronous
message passing between threads in which integer values are passed
from the producer to the buffer, and from the buffer to the consumer.
Solutions must strictly use threads with a synchronous message passing
implementation. Solutions in Java may use the following:
public class Selectable {
public void guard(boolean g);
}
public class Channel<T> extends Selectable {
public synchronized void send(T v);
public synchronized T receive();
}
public class Select {
public void add(Selectable s);
public synchronized int choose();
}
It is recommended that the consumer has a separate get request (to
request data from the buffer thread) and get reply (to receive the
requested data) channels; the producer needs only a single put channel
to send data to the buffer thread.
Place your answer in the directory Q4. If
programming in Java, use the provided Q4/BoundedBuffer.java
as a template. If using another language, prefix your main program
file with the name boundedbuffer, and your solution should
produce the same output and have the equivalent sleep behavior as
for BoundedBuffer.java.
[14 marks]
QUESTION 5: Architectures [20 marks]
- Three programming languages for concurrency are
Ada95, Java and C/Posix. Briefly describe the characteristics
of each in terms of level of abstraction, support for
consistency (conversely the susceptibility to errors) and
efficiency. Illustrate this on a specific simple example such
as a bounded buffer implementation.
Place your answer in the file Q5/Q5.txt.
[6 marks]
- Write a (C) program to implement the compound shell command
by using the fork() system call and each process executing
one of the sub-commands. It may be assumed that the
ls and wc executables are in the /bin
and /usr/bin
directories, respectively.
Place your answer in the directory Q5/Q5p2. If
programming in C, use the provided Q5/p2/combcmd.c as a
template. If using another language, prefix your main program file
with the name combcmd.
[7 marks]
Hint: you may find the execl(), pipe() and
dup2() system calls useful.
- State two limitations of Posix pipes as a form of inter-process communication.
Place your answer in the file Q5/Q5.txt.
[2 marks]
-
Consider a user wishing to connect via the Secure Shell remote login
client ssh to a remote server at IP address
150.203.24.2. The remote server has a Secure Shell daemon
process (sshd) listening on port 22.
Describe the series of socket system calls that both (i) the
ssh process on the local host and (ii) the sshd on the
remote host must perform in order to establish a connection.
Place your answer in the file Q5/Q5.txt.
[5 marks]
Hint: your answer is likely to include the system calls
socket(), connect(), bind(), listen() and
accept().
QUESTION 6: Distributed Systems [13 marks]
-
The User Datagram Protocol (UDP) is an unreliable protocol,
whereas the Transport Control Protocol (TCP) is deemed reliable.
Why is UDP useful? Give an example in distributed systems
where the UDP is preferred over TCP.
Place your answer in the file Q6/Q6.txt.
[2 marks]
-
The following diagram shows a system of three processes using
Lamport's algorithm for logical time. The initial value of the
logical time in each process is shown in the first box in each
line. Timing events are indicated by subsequent boxes; these may or
may not be associated with message passing (indicated by arrows).
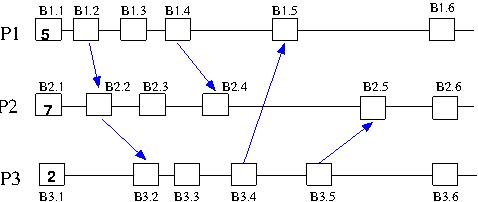
Enter the value of the logical clock
which should appear in each of the labelled square boxes.
Place your answer in the file Q6/Q6.txt.
[3 marks]
- Consider a system using transactions with two-phase
locking. Explain why using reader/writers locks is useful, and discuss
whether, for a typical scenario, different priorities should be given
to readers or writers.
Place your answer in the file Q6/Q6.txt.
[2 marks]
- Explain why a multicast over a group of processes
is important in the context of distributed systems
Place your answer in the file Q6/Q6.txt.
[2 marks]
- State the CAP Theorum as it applies to distributed systems.
Describe a scenario where it might be preferable to sacrifice the `C'
aspect of the theorum in favor of the `A' and `P' aspects.
Place your answer in the file Q6/Q6.txt.
[4 marks]
